Ghost SSL 证书过期的解决办法
目录
问题
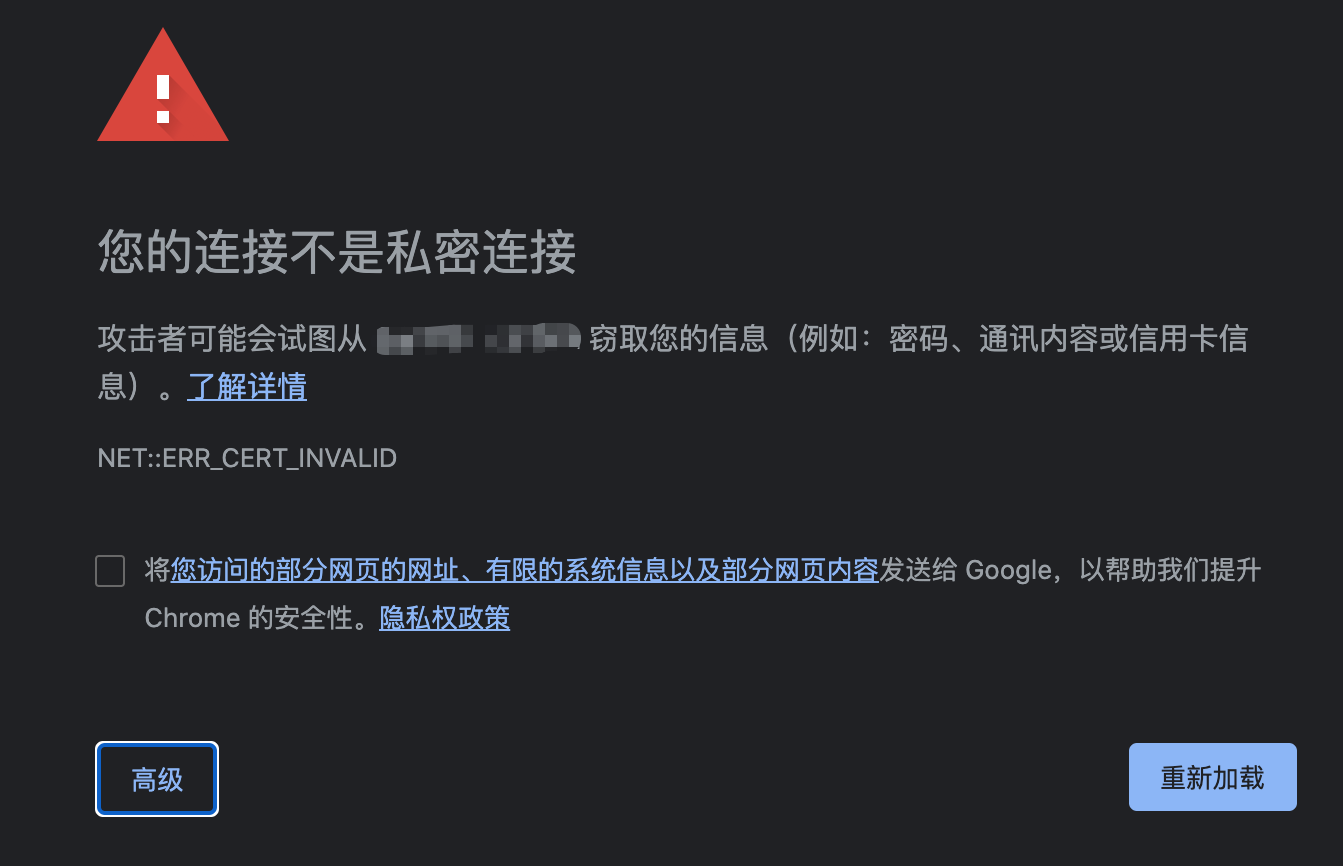
今天访问我的 Ghost 博客 的时候,发现进不去了:
网上找的图,不过就是这个样子,当时忘了截图
点击 高级 也没有进去的链接,而且页面地址前面写着”不安全“,证书显示也已经过期一个月了。而且我自己部署的 flask 服务也访问不了了。
原因
Ghost 本身其实会自动 renew 证书,可使用如下命令查看定时任务:
1 | $ sudo crontab -l |
有这个输出就表示会自动 renew。但是根据网上的说法,Ghost 没有及时升级 /etc/letsencrypt/acme.sh 版本,造成 renew 失败之类的。
我看同目录下的 account.conf 中有一行是这样的:
1 | #AUTO_UPGRADE="1" |
自动升级默认是被注释掉的,不过我也不能百分比确定取消注释就会自动升级。具体我也不是很懂,就不多说了,就提一嘴。
解决
所以总而言之,就是要升级 acme.sh 然后重启 Ghost。
- 进入 acme.sh 目录:
1
cd /etc/letsencrypt
- 备份原文件:
1
sudo cp acme.sh acme.sh.bk
- 升级:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15sudo ./acme.sh --upgrade
./acme.sh: line 6192: cd: /home/username/.acme.sh: No such file or directory
[Fri Apr 30 09:47:22 CST 2021] Installing from online archive.
[Fri Apr 30 09:47:22 CST 2021] Downloading https://github.com/Neilpang/acme.sh/archive/master.tar.gz
touch: cannot touch '/home/username/.acme.sh/http.header': No such file or directory
[Fri Apr 30 09:48:36 CST 2021] Extracting master.tar.gz
[Fri Apr 30 09:48:36 CST 2021] It is recommended to install socat first.
[Fri Apr 30 09:48:36 CST 2021] We use socat for standalone server if you use standalone mode.
[Fri Apr 30 09:48:36 CST 2021] If you don't use standalone mode, just ignore this warning.
[Fri Apr 30 09:48:36 CST 2021] Installing to /home/username/.acme.sh
[Fri Apr 30 09:48:36 CST 2021] Installed to /home/username/.acme.sh/acme.sh
[Fri Apr 30 09:48:36 CST 2021] Good, bash is found, so change the shebang to use bash as preferred.
[Fri Apr 30 09:48:37 CST 2021] OK
[Fri Apr 30 09:48:37 CST 2021] Install success!
[Fri Apr 30 09:48:37 CST 2021] Upgrade success! - 升级后的文件是放在 home 目录下的,所以要 cp 过来:
1
sudo cp ~/.acme.sh/acme.sh .
- 手动执行一次定时任务。注意加上 —force,原因:sudo · acmesh-official/acme.sh Wiki
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25sudo "/etc/letsencrypt"/acme.sh --cron --home "/etc/letsencrypt"
[Fri Apr 30 09:53:20 CST 2021] ===Starting cron===
[Fri Apr 30 09:53:21 CST 2021] Renew: 'northcloudgate.com'
[Fri Apr 30 09:53:22 CST 2021] Using CA: https://acme-v02.api.letsencrypt.org/directory
[Fri Apr 30 09:53:22 CST 2021] Single domain='northcloudgate.com'
[Fri Apr 30 09:53:22 CST 2021] Getting domain auth token for each domain
[Fri Apr 30 09:53:25 CST 2021] Getting webroot for domain='northcloudgate.com'
[Fri Apr 30 09:53:25 CST 2021] Verifying: northcloudgate.com
[Fri Apr 30 09:53:30 CST 2021] Success
[Fri Apr 30 09:53:30 CST 2021] Verify finished, start to sign.
[Fri Apr 30 09:53:30 CST 2021] Lets finalize the order.
[Fri Apr 30 09:53:30 CST 2021] Le_OrderFinalize='https://acme-v02.api.letsencrypt.org/acme/finalize/64051473/9381845272'
[Fri Apr 30 09:53:31 CST 2021] Downloading cert.
[Fri Apr 30 09:53:31 CST 2021] Le_LinkCert='https://acme-v02.api.letsencrypt.org/acme/cert/03175a17da415b526b37dedf518750770ddc'
[Fri Apr 30 09:53:32 CST 2021] Cert success.
-----BEGIN CERTIFICATE-----
CERTIFICATE CONTENT==
-----END CERTIFICATE-----
[Fri Apr 30 09:53:32 CST 2021] Your cert is in /etc/letsencrypt/northcloudgate.com/northcloudgate.com.cer
[Fri Apr 30 09:53:32 CST 2021] Your cert key is in /etc/letsencrypt/northcloudgate.com/northcloudgate.com.key
[Fri Apr 30 09:53:32 CST 2021] The intermediate CA cert is in /etc/letsencrypt/northcloudgate.com/ca.cer
[Fri Apr 30 09:53:32 CST 2021] And the full chain certs is there: /etc/letsencrypt/northcloudgate.com/fullchain.cer
[Fri Apr 30 09:53:32 CST 2021] Run reload cmd: nginx -s reload
[Fri Apr 30 09:53:32 CST 2021] Reload success
[Fri Apr 30 09:53:32 CST 2021] ===End cron=== - 重启 Ghost:
1
2
3
4
5cd /var/www/ghost
ghost restart
+ sudo systemctl is-active ghost_northcloudgate-com
+ sudo systemctl restart ghost_northcloudgate-com
✔ Restarting Ghost
然后,就又可以看到安全的小白锁了,证书也有效了:
彩蛋
在 Google ”您的连接不是私密连接“这个问题的时候,意外发现了一个神奇操作:
”thisisunsafe“:这是我见过的最神奇最离奇的操作了,没有之一。当你遇到”您的连接不是私密连接“错误的时候,直接在当前页面”凭空“输入这个字符串,就可以进去页面了。注意是凭空,不是地址栏,你看不到你所输入的东西。#有用而有趣的冷知识https://t.co/TnZ5a5o5LN
— Alan Lee (@bluekirin93) April 30, 2021
即,当你遇到“您的连接不是私密连接”错误的时候,直接在当前页面“凭空”输入 thisisunsafe,就可以进去页面了。注意是凭空,不是地址栏,你是看不到你所输入的东西的。
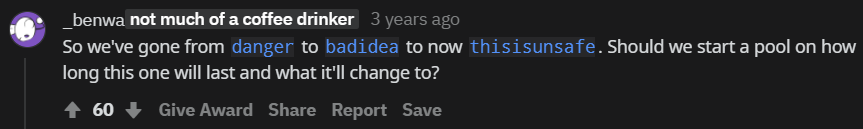
而且根据 reddit 上的说法,
- 这个 bypass word 之前是
badidea,再之前是danger。 - Chrome 65 的时候把
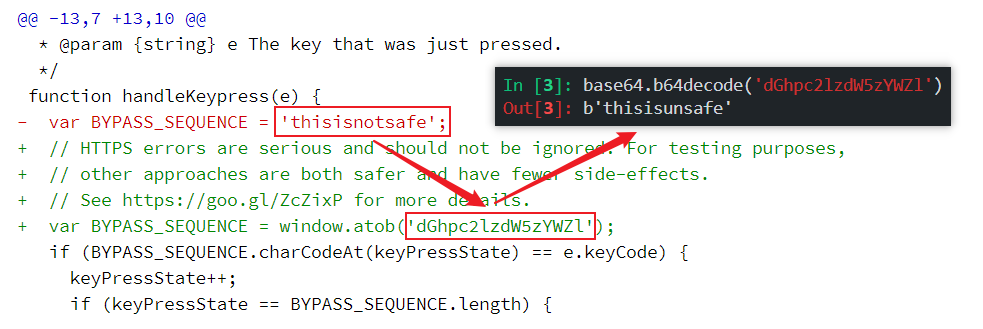
badidea改成了thisisnotsafe又改成了thisisunsafe。而且还用 base64 加密了。
此外前文提到的 flask 服务也恢复正常了。
Reference
- Ghost博客网站证书过期,怎么办?
- 事故记录—SSL证书过期
- Chrome 65 replaces the “badidea” bypass keyword with “thisisunsafe” : sysadmin
- Diff - d8fc089b62cd4f8d907acff6fb3f5ff58f168697^! - chromium/src - Git at Google
- THIS IS UNSAFE (and a Bad Idea) - DEV Community
![博客恢复]](https://i.loli.net/2021/05/01/pxnyQzWXCo7EMgh.png)